FBI Tackles DNSChanger Malware Scam
Fbi takes mike lindell s phone fbi takes phone fbi takes trump s passport fbi takes safety deposit boxes fbi takes congressman s cell phone fbi takes brians parents into custody fbi takes gold
FBI tackles DNSChanger malware scam
If you've been familiar with the malware scene over the past few years, you know one of the prominent attacks on personal computers and information has been the DNSChanger scam.
DNSChanger is a Trojan horse that was distributed in many forms, and when installed it actively changes the infected system's DNS settings to rogue servers that redirect legitimate searches and URLs to malicious Web sites that attempt to steal personal information and generate illegitimate ad revenue for the scammers.
The DNSChanger malware was first discovered around 2007, and since this time has infected millions of computers, around 500,000 of them being in the U.S., and through these computers the criminals have reportedly pulled in around $14 million in stolen funds. This success spurred the criminals to branch out from targeting Windows PCs to other platforms that include the Mac OS and also networking hardware such as routers, so entire networks could be scammed.
The Mac variants of the malware, found starting in 2008, were known as OSX.RSPlug.A, OSX/Puper, and OSX/Jahlav-C. These have been distributed through pornographic Web sites disguised as required video codecs for QuickTime, and as with the Windows versions, when installed the Trojan would change the system's DNS settings to servers that would redirect legitimate Web URLs to malicious sites.
To combat this threat, a number of malware detection tools were quickly developed to specifically target and remove the DNSChanger malware, and most antivirus utilities have proper definitions for detecting and removing it, but the threats have still been out there and affecting systems where they could.
Recently the FBI put a major dent in the DNSChanger operation with Operation Ghost Click, which recently ended in the arrest of six Estonian nationals who are accused of being integral in running the fraud ring. Along with the arrests, a number of computer systems were seized that the FBI says were being used as rogue DNS servers, but instead of just being shut down they were replaced with legitimate servers.
This action means that many of the millions of computers that are still currently infected with the DNSChanger malware should now be receiving healthy DNS server activity even if the DNS server IP addresses on their systems are changed by the malware.
This is definitely a helpful step in the right direction for unsuspecting individuals who may be affected; however, it is not a guarantee of safety for affected systems, especially since the malware and its variants could still be running on the systems.
Besides running antimalware utilities to detect and remove the DNSChanger malware, computer owners can manually check the DNS settings on their systems to see if they are affected. This is perhaps the best option since even if there is no malware on a specific computer, a compromised router will give rogue DNS information to all systems that connect to it.
To check your DNS servers, you will need to manually enter their information in the FBI's DNS-checking Web site, which will issue you a warning if the server is a compromised one. To do this in OS X, follow these directions:
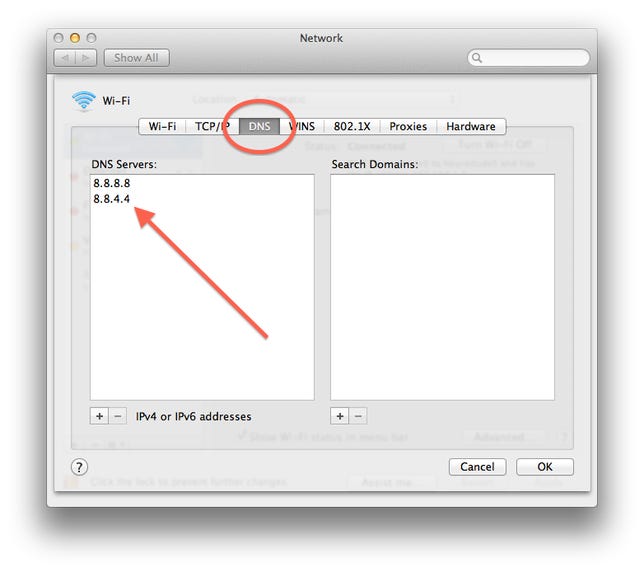
- Open the Network system preferences.
- Select your network connection (the active one will be at the top of the list).
- Click the "Advanced" button, and in the new window click the "DNS" tab.
- Note the DNS Server IP addresses in the list on the left (some may be grayed out).
Compare the DNS servers' IP addresses to the following FBI-provided list of rogue DNS servers (PDF). If they fall in any of these ranges, then your system may be using one of the rogue DNS servers.
85.255.112.0 through 85.255.127.255
67.210.0.0 through 67.210.15.255
93.188.160.0 through 93.188.167.255
77.67.83.0 through 77.67.83.255
213.109.64.0 through 213.109.79.255
64.28.176.0 through 64.28.191.255
An easier method for checking the IP addresses is to enter them one at a time in the FBI's Rogue DNS Checker Web site, which will inform you whether or not the IP address is valid.
Repeat this check for every network connection option in OS X (including AirPort, Ethernet, and others like FireWire), since the DNS configuration for each is separate. If the server IP addresses in the DNS list are grayed out and cannot be edited, this means the servers are configured in your router and can be modified by going to your router's settings (usually done through a Web interface).
Do keep in mind that the DNSChanger malware is from around 2008 and is not anything new, but this latest news is a good reminder to check and be sure your system's network settings are as they should be. In addition to checking your network settings, you can check for the malware with most updated malware scanners or by downloading and running the DNSChanger Trojan removal tool from SecureMac.com. Because the malware has been around for a long time and has not changed much for OS X systems, most reputable malware scanners should easily detect it.
Questions? Comments? Have a fix? Post them below or e-mail us!
Be sure to check us out on Twitter and the CNET Mac forums.
Source
